Our five main services
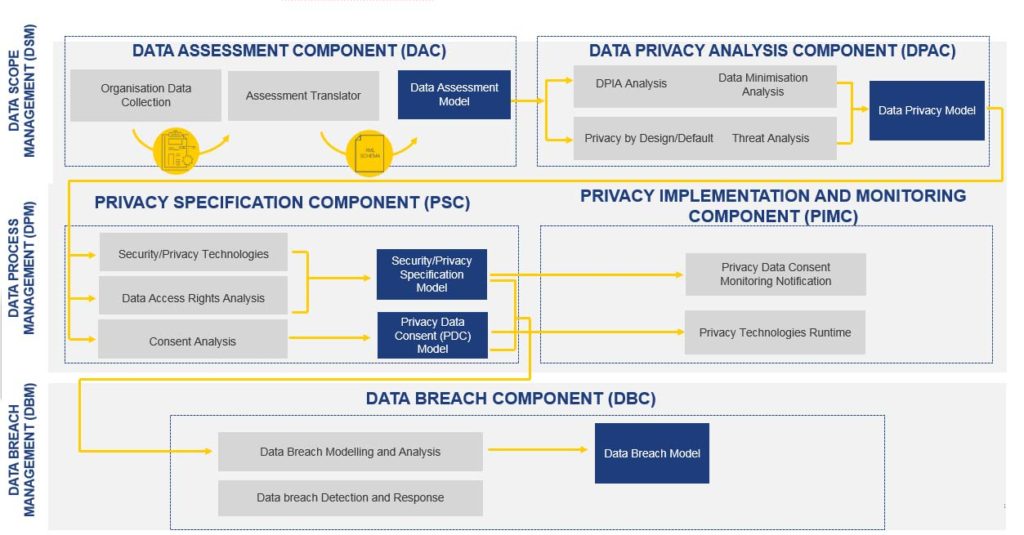
The DEFeND platform provides 5 main services to organisations and relevant stakeholders: Data Scope Management Service, Data Process Management Service, Data Breach Management Service, GDPR Planning Service and GDPR Reporting Service. Each one of these services assists organisations to collect, analyse and operationalise different aspects and articles of the GDPR and provide appropriate reporting capabilities. To support those services, the platform consists of five (5) back-end components: Data Assessment Component, Data Privacy Analysis Component, Privacy Specification Component, Privacy Implementation and Monitoring Component, Data Breach Component. Each component includes a number of modules aiming to deliver functionalities. The modules will be developed in WP3 by enhancing software tools, services and frameworks of the project partners. These components have been developed under various different national and international projects